Summary: Modern optical mice can sense tiny desk vibrations from nearby speech. With signal processing and AI, parts of that speech can be reconstructed. It’s clever and real—but niche. The best defenses are simple: keep unknown software off your machine, damp the vibrations, and lower sensor sensitivity when you don’t need it.
What “Mic‑E‑Mouse” is
Researchers at UC Irvine introduced Mic‑E‑Mouse, a side‑channel that uses a mouse’s optical sensor as a proxy “microphone.” When you talk near a hard desk, your voice creates micro‑vibrations. High‑DPI, high‑polling sensors pick up some of that motion. A user‑space app can read the raw data stream and, after digital filtering and a neural cleanup step, recover parts of the speech signal.
• Research paper: Invisible Ears at Your Fingertips (arXiv)
• Project page + demo: Mic‑E‑Mouse (Google Sites)
• News explainer: eSecurityPlanet and The Register
How it works, in plain steps
- Speech → desk vibrations. Your voice shakes the desktop a little.
- Sensor picks motion. A high‑DPI mouse samples the surface fast enough to capture parts of that shake.
- App reads the stream. Software in user space records the pointer packets.
- DSP + AI clean the signal. Filtering, resampling fixes, and a neural spectrogram filter boost intelligibility.
- ASR transcribes. Automatic speech recognition recovers words with roughly 42–61% accuracy in controlled tests.
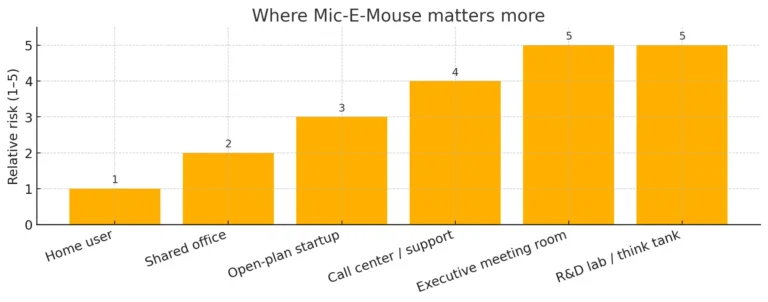
Does this matter for everyone?
For most home users, risk is low because the attack still needs code running locally to read and exfiltrate the mouse data. The risk goes up in places where sensitive talk happens near desks or where untrusted software can run: open offices, support floors, executive areas, and labs.
Quick, practical mitigations (start here)
- Block the easy path in: least‑privilege accounts, allow‑listed apps, monitored EDR/antivirus, and tight install policies.
- Dampen the signal: use thick, soft mousepads/desk mats to decouple the mouse from the desk.
- Turn down sensitivity: when not gaming, lower DPI and polling rate to reduce useful bandwidth.
- Stay updated: keep mouse firmware/drivers current; watch for vendor advisories.
- Enterprise controls: where feasible, restrict or monitor access to raw HID/pointer streams from user‑space.
- Operational habits: move sensitive conversations to soft rooms or add background noise.
What the researchers actually measured
This is not an instant wiretap. In controlled conditions, the team reported ~42–61% speech‑recognition accuracy (datasets: AudioMNIST, VCTK). Results depend on mouse model, DPI/polling rate, desk material, distance, and ambient noise. Real‑world performance will vary.
Who should act now
- Security‑sensitive workplaces (support, finance, legal, R&D): apply the mitigations and log processes that access pointer streams.
- Leaders and spokespeople: hold private talks away from hard desktops; keep machines locked down.
- Streamers/podcasters: your audio hygiene is already high—focus on software hygiene and driver updates.
Further reading
- Paper: Invisible Ears at Your Fingertips (arXiv) • PDF
- Project page: Mic‑E‑Mouse (Google Sites)
- Press coverage: eSecurityPlanet, The Register
Related on BlogsTrade: Learn how we connect security with performance and ranking. Explore our Services, get help via Contact us, or read What is SEO (search engine optimization)? for the basics.